 Security is the state of a system or object (housing, apartment, etc.), in which the impact of external and internal factors does not interfere with its activities
Security is the state of a system or object (housing, apartment, etc.), in which the impact of external and internal factors does not interfere with its activities
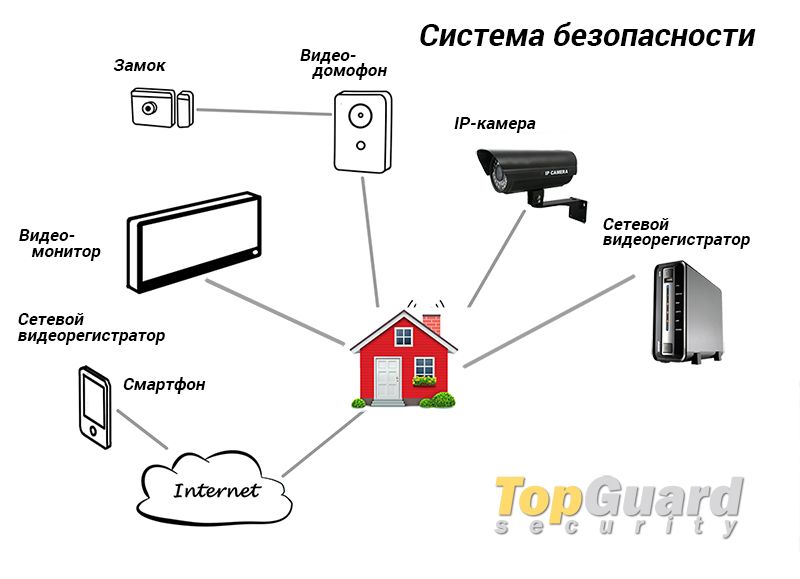
Home security systems
Security is the state of a system or object (housing, apartment, etc.), in which the impact of external and internal factors does not interfere with its activities.
Currently, there are many objects of private and state property that use security security systems of various types.
For the implementation of protection, various systems have been developed, which can be divided into separate types:
- warning systems;
- security systems for summer cottages;
- security systems for private houses;
- fire extinguishing systems;
- power supplies of the security and fire alarm system;
- GSM-systems for object security;
- video surveillance systems.
Choice of security systems with notification
In case of violation of the security regime or the occurrence of an emergency, information transmission means are installed at the facility for notification. The objects should have a SOUE-system for warning and evacuation control. This system can be used in 2 modes:
Manual notification mode. It is carried out through the loudspeaker communication with the help of the dispatcher or through the panic button, if we are talking about the console protection;
Automatic option. It is carried out with the help of several sources through the broadcasting of an alarm signal and the transmission of an information message.
Modern automatic systems allow:
- transmit and receive alarms according to a given program;
- replace messages after a certain period of time;
- control the signal transmission system;
- to transmit a voice message to employees and officials in accordance with a given program.
Installation and features of security security systems for summer cottages and private houses
Security security systems can be of several types:
- autonomous alarm;
- security alarm systems using GSM;
- burglar alarm with signal transmission over a telephone line.
The autonomous alarm system consists of sensors that detect violation of the security mode. When the system is triggered, it generates light and sound signals, warning neighbors about illegal entry into a residential building. In this case, neighbors must call security or a police squad to check the facility where the alarm was triggered. Security systems for private houses can improve the security of property and reduce the incidence of theft.
Security alarm system using a GSM signal. When installing this security system, mobile communication is used. The alarm signal is sent to the owner of the facility and to the security console of the organization performing safe operation and protection of home ownership. A burglar alarm system using a telephone line operates on the same principle. The signal about the violation of the regime is transmitted to the security console, which goes to the object and checks it.
For signal transmission, the security system uses a special secure channel with a frequency of 433 MHz, which is received from sensors detecting intrusion on the object.
Various sensors can be installed in the house:
- infrared passive motion sensor, detects the movement of thermal radiation in the room;
- magnetic contact sensors;
- smoke response sensors;
- sensors for responding to the movement of an object with transmission of a signal at a radio frequency;
- vibration sensors reacting to the slightest vibrations;
- infrared beam sensors react to the crossing of the laser beam by a foreign object.
It should be noted that the sensors used in the wired system have a larger radius of detection and fixation of violations of the security mode. For wired sensors, the maximum response range is no more than 100 meters.
Equipping facilities with security systems with the ability to respond and use fire extinguishing equipment
Security and fire alarm is a complex of special technical means designed to detect the source of fire and unauthorized violation of the security regime.
The system includes:
- control panel;
- control partings;
- sensors;
- control devices;
- various warning devices;
- power supplies of the fire alarm system.
For automatic fire extinguishing, AUPT is used - an automatic fire extinguishing installation, which is brought into operation in an automatic mode when the control sensors for detecting a fire are triggered. The reason for the activation of the fire extinguishing system may be increased smoke pollution in the premises or an increase in the permissible temperature in the premises.
AUPT are produced in several types, depending on the substance used to extinguish the fire:
- water;
- foamy;
- gas;
- powder;
- aerosol.
For power supply of fire alarm and fire extinguishing systems, power supplies are used, which provide power supply in the backup and uninterruptible power supply mode.
Using video surveillance systems
For constant monitoring of objects, video surveillance systems with video cameras are used. Video surveillance can be performed in on-line mode, as well as record all events on the video recorder.
The video surveillance kit includes:
- cameras (analog or digital) in the amount of 2 to 8 pcs .;
- video recorder;
- power unit;
- connecting wires;
- control and management unit.
Cameras can be installed inside the house and around the perimeter of the site.
GSM systems for burglar alarms
To transmit a GSM signal, security systems use a GSM / Wi-Fi network, which is capable of operating at temperatures from -40 C to + 50 C and is highly reliable. The GSM system can be equipped with an IP camera that works in a Wi-Fi network and uses GSM as an additional signal transmission channel.
The use of security systems significantly increases the level of security of houses and ensures the safety of property.
GSM signal interception protection
There are three generations of wireless communication: 2G, 3G, 4G. The most popular standard is 2G, which means it has the largest coverage area. It was commissioned in the early nineties. Since this standard is more than twenty years old, it has a number of security problems: one-way authentication and the ability to establish a connection without encryption.
There is a telephone and a base station. The phone has an unrecoverable key on the SIM card, which is used for authentication. On the operator's side, for each authentication, a random number, sres, and a session encryption key (Kc) are generated. The base station sends a random number to the phone, the phone sends it to the SIM card. The SIM card, in response, returns two values - sres and Kc. Sres is returned to the operator. By comparing sres, the operator identifies the subscriber. After that, a command is issued for encryption, which occurs with the help of Kc.
It can be seen from the above algorithm: nothing prevents you from replacing the base station, replacing encryption with the absence of encryption. Using this vulnerability, an attacker can listen to us. To implement a full-fledged interception, you will need a virtual base station (BTS), a decoder and a phone emulator. An interceptor in the form of such a system would be quite expensive.
A simplified version can be used. There is a virtual base station and internet. Interception is carried out via the Internet via VoIP. This option has a number of limitations. That is, the connection will be one-way. Through VoIP, the subscriber will be able to make calls, but will not be able to receive calls.
Using this vulnerability, it is still possible to implement an IMSI-Catcher and a signal blocker. IMSI-Catcher is a system that receives identifiers of mobile devices in range and hangs them up. That is, subscribers return to the network of a real telecom operator, but their identifiers have been received. The signal blocker works in much the same way as the IMSI-Catcher, but after the authentication process it accepts the subscriber. The subscriber is at this virtual base station and no services are available to him.
There are a number of signs that a signal is being intercepted:
- Strong signal.
- Large coefficient C2. The C2 factor is used by the operator to balance the load between cells.
- Lack of Paging Request. These are packets responsible for the request to establish a channel with a subscriber.
- Lack of services (EDGE, USSD, and so on).
- Definition of "jammers" (signal suppressor).
- No neighbors (all neighbors are from another LAC).
- Lack of encryption.
- Opening a channel without committing a transaction.
Considering all these signs, you can try to find the attacker using SDR. This is a radio platform that allows you to tune to the desired frequency, receive a signal, demodulate and decode it already on the computer. At the output, we can receive a spectrum and a broadcast channel. According to the GSM standard, there are a number of radio signals that must be observed for electromagnetic compatibility. Accordingly, by looking at the spectrum, signs of interception are revealed. Analyzing them, we can conclude: we are on a real base station or on a virtual one.




